 |
| Mikrotik Router Mikrotik Hotspot Prevention of WannaCry Malware Deployment with Mikrotik Router |
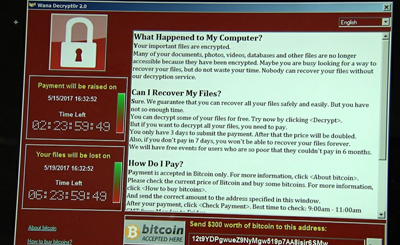
Ransomware WannaCry the last few days has horrendous the world of IT due to its massive attack occurred in many countries around the world.
Based on information from Microsoft, this malware takes advantage of security holes in the SMB feature used for file share in OS Windows. Iit is also known to attack through the RDP feature. SMB runs on the network at UDP 137.138 and TCP 137.139, 445. While RDP on port 3389.
 |
| Mikrotik Router Mikrotik Hotspot Prevention of WannaCry Malware Deployment with Mikrotik Router |
This malware attacks by way of encrypting the data on the victim's computer.In other words, when infected with this malware the data / files on the victim's computer can no longer be accessed. To be able to re-access our data, the malware authors demanded a ransom.
In Indonesia alone Kominfo has provided tips and preventive steps that can be done on the computer side. Ie by disabling SMB and RDP functions, update windows patch, backup data / files on other storage and so on.
However, there is no harm if we add a security method in our network system. On the Mikrotik Router, we can use the Firewall Filter feature to block the ports and protocols used by WannaCry malware in spreading
Firewall Filter
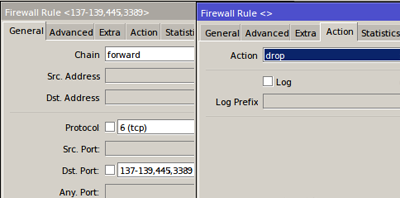
The first method that can be applied is to create a firewall filter rule on Mikrotik Router to prevent data exchange on protocol and port used by WannaCry malware.
 | |
|
This rule will work for different subnet traffic, either between LAN and from public / internet.
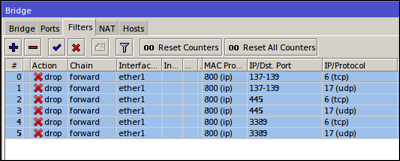
Bridge Filter
This method can be applied to a network where all hosts are in the same subnet / segment ip and under bridging conditions. The step defines the matcher and then use action = drop
 | |
|
 | |
|
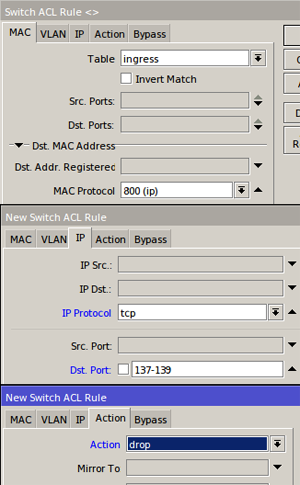
ACL Switch
For prevention on a subnet network other than using the bridge filter method can also use the ACL feature on manageable switches, for example in the following Mikrotik Cloud Router Switch products
 | |
|
Also create a new rule for blocking TCP 445 and 3389 to complete the above rule to make it more secure.
With the implementation of the rule temporarily between hosts / computers can not use the feature file sharing via SMB or remote desktop. As an alternative it can use other vpn applications that have similar RDP functionality while file exchange can be done through cloud service or public server or offline. Also should not carelessly download files or run programs that come from sources that are not trusted.
No comments:
Post a Comment